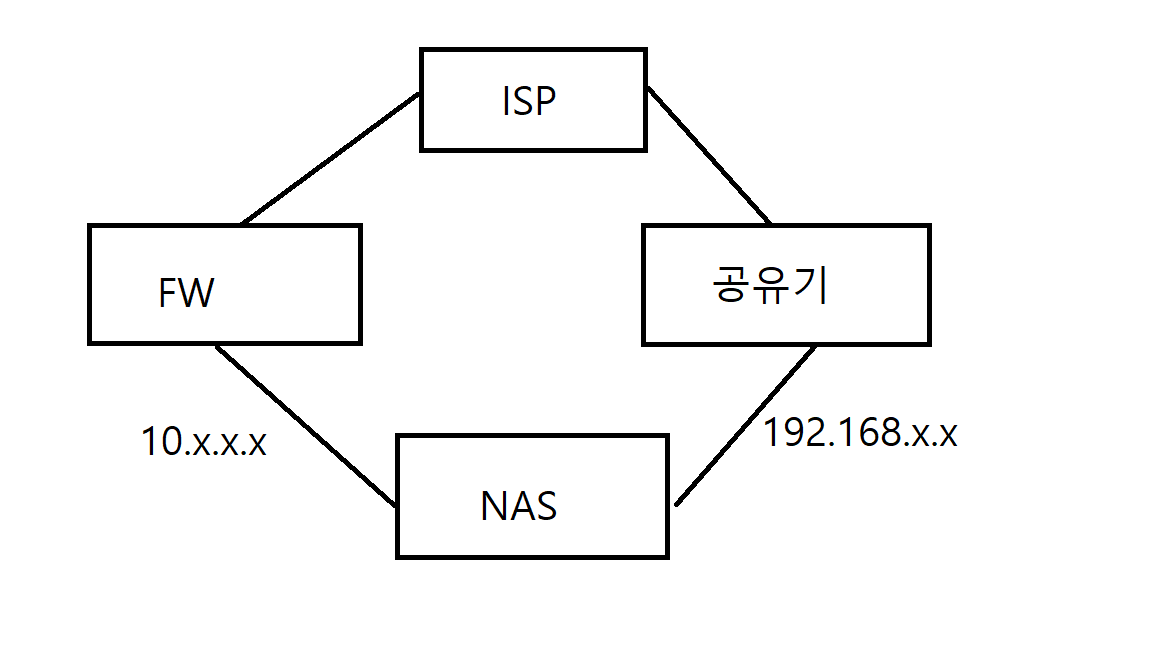
현재 synology.me로 접근시 흐름도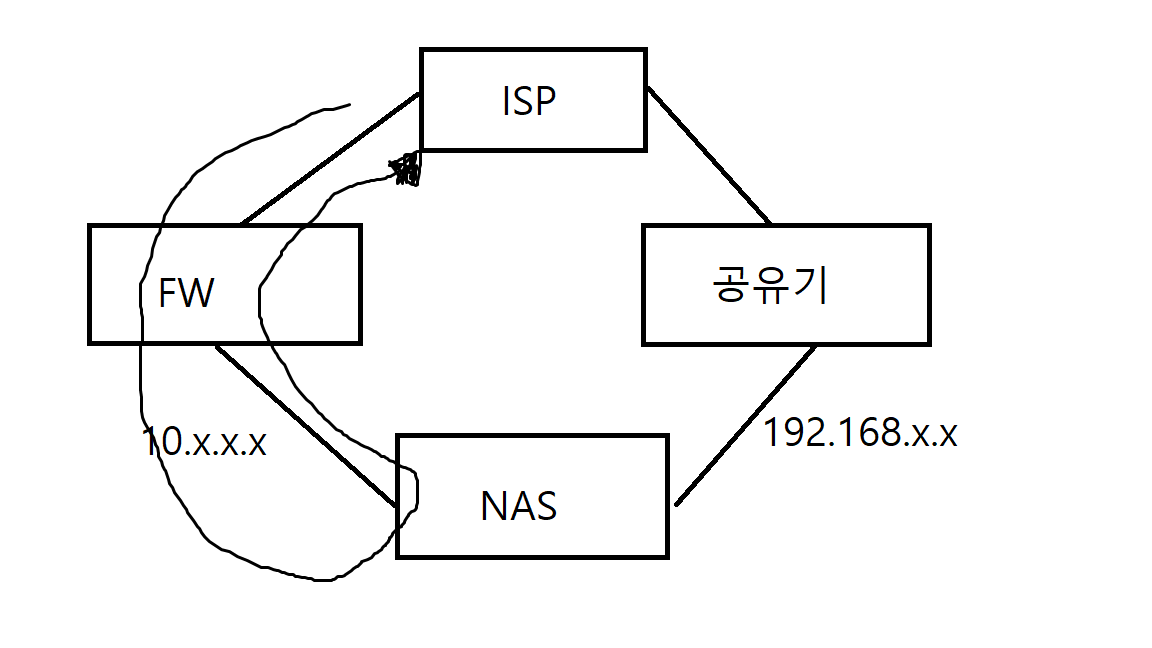 현재 iptime.org로 접근시 흐름도
현재 iptime.org로 접근시 흐름도
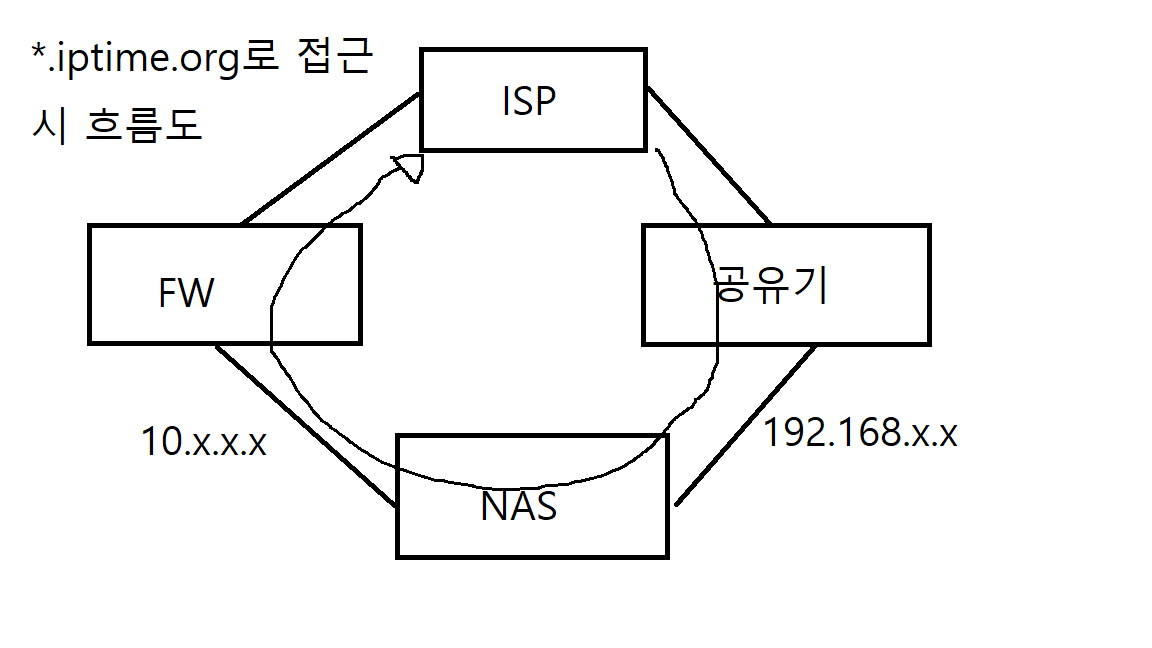
제가 원하는 흐름도
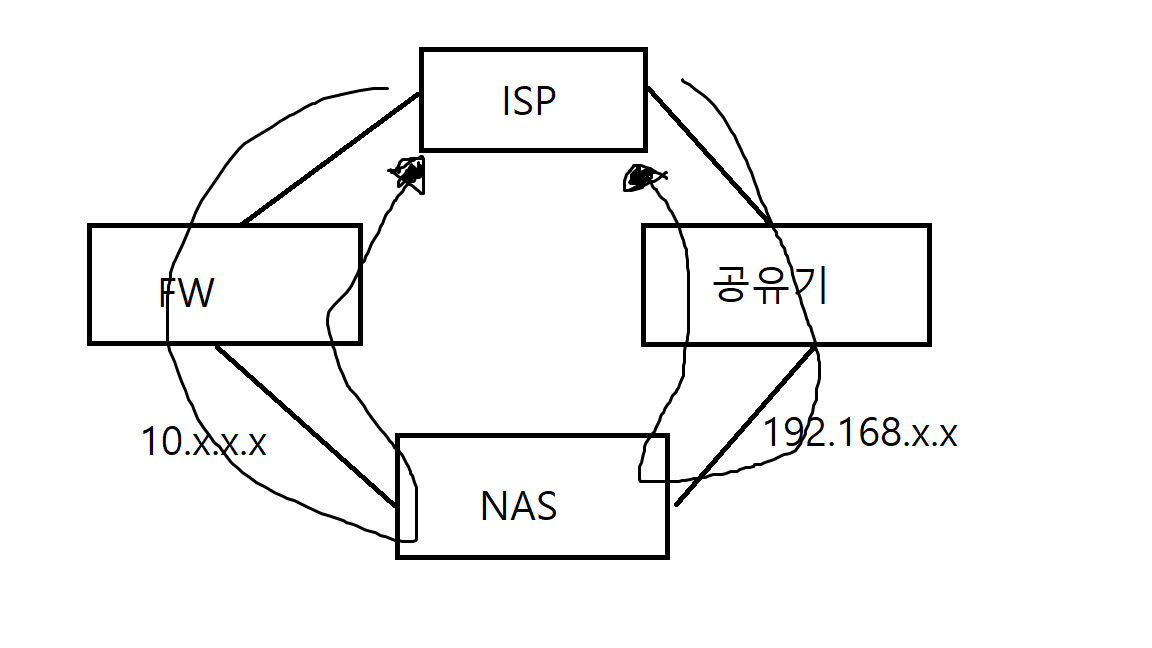
위와 같이 네트워크가 구성되어있고
FW과 공유기는 별도의 외부 공인IP를 받은 상태이고 Synology NAS의 기본G/W는 FW를 타게 되어있습니다.
현재 외부에서 *.synology.me:5000로 접근시에는 FW을 타고 NAS로 접근하게 되어있는 상태이고,
공유기 *.iptime.org:5000를 통해서도 NAS로 접근하게끔 하고싶은데
*.iptime.org:5000로 접근하면 자꾸 디폴트GW로 빠져서 결국 통신이 되지 않습니다...
혹시 이런 네트워크 구조에서 공유기를 타고 NAS로 들어올경우 NAS에서 다시 공유기를 타고 외부로 나가게끔 할 수 있는 방법이 있을까요?




NAS 입장에서 모르는 IP를 어디로 보낼지를 결정하는 것이 default g/w 설정입니다.
일단 두개의 랜카드 중 하나가 디폴트로 설정되는데요,
나머지는 대역별로 나누어서 라우팅에 추가해줍니다. 시놀로지도 네트워크에서 Static Route를 잡아줄 수 있습니다.
그래서 실제로는 출발점이 어디냐에 따라 어느 쪽으로 흘려보낼건지 결정할 수 있는데요. 같은 곳에서 fw, iptime 왔다갔다 접속하면서 제대로 되기는 어려울 것 같습니다.
한가지 방법이 있다면, vpn을 이용하면 될것 같은데요.
공유기의 vpn을 이용하면, 단말이 192 ip를 받을 것이기 때문에 공유기를 통해서 다시 나가게 되는 거죠.
외부에서 IPtime 거처서 시놀로지로 들어올때 세션 정보를 통해
다시 IPtime을 통해서 접속 되는게 정상입니다...
즉, iptime.org로 접근시 흐름도 자체가 이상합니다.
이게 되려면 최소한 ISP와 연결된 FW, IPtime 사이에
VIP로 공인IP를 통일시켜서 연결되어야되서 L4가 필요합니다..
디폴트 GW는 시놀로지 자체에서 외부 통신 요청에 대해서
해당 디폴트 GW를 통해 통신이 이뤄지게 하는 다중 GW에 대한 우선순위일 뿐입니다.
혹시 시놀로지 GW 설정이 정상인지 확인해 보셨나요??
추가적으로...
*.iptime.org 와 *.synology.me에 대한 IP가 동일한지 확인해보시기 바랍니다.
iptime.org
synology.me는 각각 IP가 다르구요
저는 OpenWRT에서 아래와와 같이 사용중입니다.
2-WAN에 2-LAN으로 각각에서 오는 패킷을 fwmark하여 라우팅합니다.
제가 쓰고 있는 스크립트를 정리해봤는데.. 짜집기 하면서 틀린게 있을 수 있습니다.
LAN_SERVER_IF=bond0.10
LAN_SERVER_NET=10.0.0.0/8
LAN_SERVER_RTNAME=rt_lan_server
LAN_SERVER_FWMARK=101
WAN_USER_IF=veth0_b
LAN_USER_IF=bond0.30
LAN_USER_NET=192.168.0.0/16
LAN_USER_RTNAME=rt_lan_user
LAN_USER_FWMARK=102
WAN_SERVER_IP=$(ip addr show dev $WAN_SERVER_IF | grep "inet " | grep brd | awk '{print $2}' | awk -F/ '{print $1}')
WAN_SERVER_GW=$(cat /var/run/net_${WAN_SERVER_IF}_router)
WAN_SERVER_NET=$(/sbin/ip route | grep $WAN_SERVER_IF | grep kernel | awk '{print $1}')
WAN_USER_IP=$(ip addr show dev $WAN_USER_IF | grep "inet " | grep brd | awk '{print $2}' | awk -F/ '{print $1}')
WAN_USER_GW=$(cat /var/run/net_${WAN_USER_IF}_router)
WAN_SERVER_NET=$(/sbin/ip route | grep $WAN_USER_IF | grep kernel | awk '{print $1}')
iptables -t mangle -N mangle_prerouting_lan_server
iptables -t mangle -A mangle_prerouting_lan_server -d $LAN_USER_NET -j RETURN
iptables -t mangle -A mangle_prerouting_lan_server -d $LAN_SERVER_NET -j RETURN
iptables -t mangle -A mangle_prerouting_lan_server -j MARK --set-mark $LAN_SERVER_FWMARK
iptables -t mangle -A PREROUTING -i $LAN_SERVER_IF -j mangle_prerouting_lan_server
iptables -t mangle -N mangle_prerouting_lan_user
iptables -t mangle -A mangle_prerouting_lan_user -d $LAN_USER_NET -j RETURN
iptables -t mangle -A mangle_prerouting_lan_user -d $LAN_SERVER_NET -j RETURN
iptables -t mangle -A mangle_prerouting_lan_user -j MARK --set-mark $LAN_USER_FWMARK
iptables -t mangle -A PREROUTING -i $LAN_USER_IF -j mangle_prerouting_lan_user
iptables -t mangle -I OUTPUT -m connmark ! --mark 0 -j CONNMARK --restore-mark
iptables -t nat -A postrouting_rule -m state --state ESTABLISHED,RELATED -j CONNMARK --restore-mark
iptables -t nat -A postrouting_rule ! -s $WAN_SERVER_IP -o $WAN_SERVER_IF -j SNAT --to-source $WAN_SERVER_IP
iptables -t nat -A postrouting_rule ! -s $WAN_USER_IP -o $WAN_USER_IF -j SNAT --to-source $WAN_USER_IP
/sbin/ip route flush table $LAN_SERVER_RTNAME
/sbin/ip rule del from $LAN_SERVER_NET lookup $LAN_SERVER_RTNAME 2>/dev/null
/sbin/ip rule del fwmark $LAN_SEVER_FWMARK lookup $LAN_SERVER_RTNAME
/sbin/ip route flush table $LAN_USER_RTNAME
/sbin/ip rule del from $LAN_USER_NET lookup $LAN_USER_RTNAME 2>/dev/null
/sbin/ip rule del fwmark $LAN_USER_FWMARK lookup $LAN_USER_RTNAME
/sbin/ip route add $WAN_SERVER_GW dev $WAN_SERVER_IF src $WAN_SERVER_IP table $LAN_SERVER_RTNAME
/sbin/ip route add $WAN_SERVER_NET dev $WAN_SERVER_IF src $WAN_SERVER_IP table $LAN_SERVER_RTNAME
/sbin/ip route add default via $WAN_SERVER_GW dev $WAN_SERVER_IF src $WAN_SERVER_IP table $LAN_SERVER_RTNAME
/sbin/ip rule add fwmark $LAN_SERVER_FWMARK lookup $LAN_SERVER_RTNAME
/sbin/ip rule add from $WAN_SERVER_IP lookup $LAN_SERVER_RTNAME
/sbin/ip route add $WAN_USER_GW dev $WAN_USER_IF src $WAN_USER_IP table $LAN_USER_RTNAME
/sbin/ip route add $WAN_USER_NET dev $WAN_USER_IF src $WAN_USER_IP table $LAN_USER_RTNAME
/sbin/ip route add default via $WAN_USER_GW dev $WAN_USER_IF src $WAN_USER_IP table $LAN_USER_RTNAME
/sbin/ip rule add fwmark $LAN_USER_FWMARK lookup $LAN_USER_RTNAME
/sbin/ip rule add from $WAN_USER_IP lookup $LAN_USER_RTNAME
예전에 문제되었던 리눅스에서 멀티 GW 설정시 라우팅 문제에 대한 부분이네요...;
그나저나 이 부분을 제품화시킨 시놀로지에서 설정상 아직도 못잡았고 있다는게 이상하네요.
방화벽쪽에서는 2세대 장비가 들어서면서 일반화된
Stateful inspection 기능으로 인한 세션기반 통신 처리가
리눅스에서는 그대로 이네요;;;
원리 참고..
모든 연결은 공유기 뒷편에 있어야 정상 아닌가요?
FW는 pfsense 방화벽이구요